Macro Systems Blog
The IoT (the Internet of Things) is a fascinating technology, as it exemplifies just how much can be accomplished when Internet connectivity is used to augment the capabilities of otherwise “dumb” devices. Alas, as fascinating as it is, the IoT is also infamous for its security issues, a reputation that attackers have been perpetuating as these devices grow more common.
AI, also known as artificial intelligence, has been a trending topic lately, with it seemingly being used for any purpose you can imagine nowadays. Alas, this has also included cybercrime.
That being said, just as AI can be a weapon for cybercriminals to utilize, it can also be a shield to help protect your business from threats. For instance, in phishing prevention.
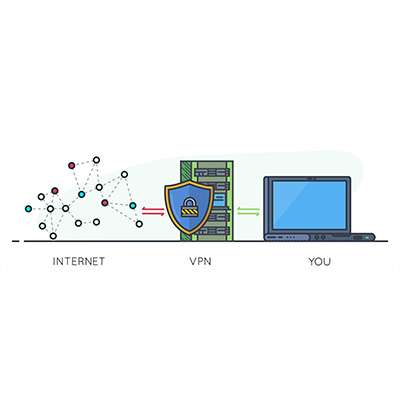
When it comes to security, one often overlooked tool is the virtual private network, or VPN. We recommend that all businesses utilize a VPN to keep remote and hybrid workers from inadvertently putting your business’ data at risk while out of the office. Listed below: why a VPN is so effective, as well as what you should look for in a business-grade VPN tool.
Businesses can't afford to grow complacent with their network security; it could make a significant difference between falling prey to an attack and remaining secure. The process of securing a network must be looked at holistically, from top to bottom. This idea of enterprise security is not new, but even a small business needs to keep it in mind, and these solutions are more accessible than you might think.
One of the reasons that information technology keeps evolving is for the sake of the user and their convenience using it. That being said, if this convenience comes at the sacrifice of your business’ cybersecurity, it just isn’t worth it. This is the crux of why we always recommend that any company seeking to use password management should invest in a reputable password management software, rather than the built-in capabilities of modern browsers.
Cyberattacks are a serious problem that all organizations face in some form or another, but there are small, everyday tasks you can do to ensure that they impact your business as minimally as possible. It takes intention and effort to protect your business and its infrastructure, but that doesn’t mean that it has to be hard. Listed below are three simple ways you can keep your infrastructure secure.
Did you know that World Backup Day is in just a few short weeks? While it is an imperative occasion for businesses to recognize, data backup should really be something you think about all the time; your backup is an integral part of the backup and disaster recovery portion of your overall business continuity.
Phishing attacks have been prominent in cybercrime the past few years, not only due to their efficacy but also because there are so many avenues wherein phishing can be attempted. The first that comes to mind is email, naturally, but you and your team need to keep these others in mind.
Take, for example, a phishing voicemail…dubbed, naturally, a “phoicemail.”
Email remains a vital cornerstone in business communications, often containing sensitive information and other data that needs to be protected. Fortunately, today's email platforms usually enable you to add a little bit of protection, so long as you know what the process looks like.
Listed below is how you can make your emails just that much more secure.
Regardless of your industry, there are going to be certain regulatory standards that you will be responsible for upholding. Many of these standards will be related in some way to your cybersecurity. Some of these cybersecurity standards are listed below, as is why compliance is so imperative for your business.
The blockchain has been a hot topic in the past few years, if only tangentially. With all the buzz about cryptocurrencies, it can be easy to forget about the underlying technology that powers it and its other applications. Listed below is a discussion about how the blockchain could be involved with security needs in the future.
Today's threat landscape is vast and unpredictable; even if you think you know enough about cybersecurity to protect your business, we bet that you don’t. It’s not even just in the business world, either, as individuals also struggle against cyberthreats, along with IT administrators. The next couple of weeks will be dedicated to cybersecurity to get across everything you need to know about it.
Whether you love them or hate them, passwords serve a critical purpose in the realm of cybersecurity. They are the first line of defense against potential threats, yet they are also notoriously easy to crack. Some of the biggest names in technology have been working on ways to get around the challenges presented by password security, including one that we are excited to highlight in today’s blog.
It hasn’t been very long since T-Mobile experienced its latest cyber attack, but alas, here we are again. Hackers have again accessed customer data, with 37 million customers being affected amongst both their prepaid and subscription-based accounts.
Listed below is an explanation of the situation, and what can be learned from it.
For a long time organizations that didn’t have any cybersecurity problems would never consider investing in additional cybersecurity tools. The decision-makers of these businesses simply didn’t find it necessary; and many of them had a point (until they didn’t). The modern threat landscape is much, much more complex than it was only a few short years ago and therefore businesses need to make a point to set up the security tools that will help them secure their network and infrastructure from threats. Listed below is a look at some strategies that work to help today's businesses secure their digital resources: