How many employees do you have who keep your organization's passwords on sticky notes stuck to their monitors? This simple, seemingly benign trick could be putting your business at risk. After all, if you can see the password on a sticky note, so too can others who happen to be wandering around the office, including potential threat actors.
Macro Systems Blog
It’s convenient for employees to reuse passwords just to make things easier for themselves; why use different passwords when you have a dozen accounts to remember passwords for? Alas, this habit will come back to bite you, especially if your business is ever involved in a data breach. These credentials could end up for sale on the dark web… and that’s just the beginning of your problems.
In a time when Internet connectivity is so critical, manufacturers have met this demand by creating products that feature the ability to connect to apps or other Internet-based dashboards. Alas for users, there is a lot that can go wrong when organizational practices don’t do enough to protect their customer’s privacy; or, simply look to exploit it. Listed below is a look at how the smart devices you rely on can be undermining your family’s privacy.
When it comes to cybersecurity, organizations have a lot to keep tabs on, even small organizations. In fact, you wouldn’t believe just how much goes into cybersecurity and why your business needs to make it a priority. Cybersecurity is more than just a buzzword on the Internet; it’s a lifeline that will keep your business secure.
There are a few occasions that we get a very apparent example of how imperative basic cybersecurity is, regardless of where you are, and this year’s National Football League draft provides one such example.
For those who don’t follow the NFL or the draft proceedings, multiple draftees received prank calls during the process, although one in particular is applicable to businesses of all kinds. Let’s examine this situation to reinforce a few important cybersecurity best practices.
We’ve all had to confirm we’re human when attempting to log into an account. This is the core purpose of what once was called CAPTCHA… the Completely Automated Public Turing test to tell Computers and Humans Apart. That being said, it seems surprising that computers don’t easily overcome these simple-seeming tests.
Listed below is why these simple tests actually are effective at differentiating between human users and automated bots.
Your Android device provides a lot of capabilities in its little frame, with many people relying on theirs to keep their lives organized. Many businesses even rely on Android mobile devices. This should only reinforce how imperative privacy and security are.
In light of this, listed below are a few simple tips anyone can do to help make a smartphone that much more secure.
X, formerly known as Twitter, has been experiencing a massive user loss for the past few weeks, with everyone from celebrities to average people evacuating from the platform. If you wish to join them for any reason, listed below is the process for fully extricating yourself and your data from this specific social media network.
There has been much debate in recent years about how companies collect, sell, and use personal data. Many businesses make extra money by selling data they collect about people. This might seem like a side effect of all the data we create online, but it can lead to some problems. Listed below is an examination of something called the "data-broker loophole," how it works, and what we can do about it.
Modern wisdom states that if you’re not paying for a product, you’re the product.
For all the good the Internet is capable of doing, it is equally capable of being dangerous… especially when data is involved. Websites and social media platforms collect data from their users and track their movements across the Internet, sell it to advertisers, and more recently, use it to train AI.
Listed below is what you can, and arguably should, do to limit these platforms' ability to do so.
Data privacy is absolutely imperative these days in both a business and individual context. In some locations, governments have introduced legislation to protect consumers, and in others, there is significant pushback in favor of fewer regulations on business. How does data privacy factor into your business’ operations?
In 2004, a service called VirusTotal was launched and quickly became a popular antivirus and malware scanner to help detect threats in various files and URLs. It became popular enough that it was officially acquired by Google in 2012 and ultimately assimilated into Chronicle, a cloud-based security operations suite for enterprise businesses. However, despite this impressive pedigree, we find ourselves able to look to VirusTotal as a sobering reminder of how fickle cybersecurity can be, with the service being the source of some limited data exposure.
Compliance is an imperative element of many businesses’ requirements, with severe penalties as a consequence if the prescribed standards are not met. Even more critically, most compliance requirements and regulations are put in place for the welfare of not only the business, but its clientele as well. This makes it important to know which apply to your business, and how to meet them fully.
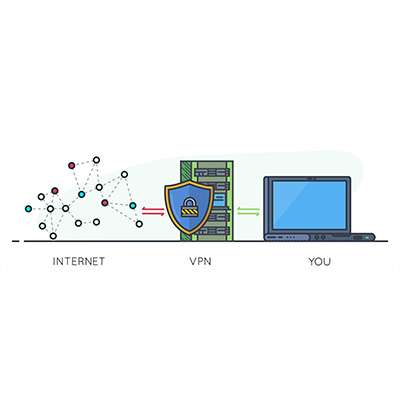
When it comes to security, one often overlooked tool is the virtual private network, or VPN. We recommend that all businesses utilize a VPN to keep remote and hybrid workers from inadvertently putting your business’ data at risk while out of the office. Listed below: why a VPN is so effective, as well as what you should look for in a business-grade VPN tool.
Who are you? While it’s a question that has been asked in all contexts with all levels of metaphysicality attached—from asking someone their name to prompting someone to follow a path of spiritual self-discovery—the growth of the metaverse once again urges us to ask it in a more literal way. When accessing a conglomeration of various services and platforms, how many identities will each user need to juggle?
We aren’t going to pretend that the investments required to preserve your business’ data security are small ones. Especially at first glance, you may very well start to question if such an investment is truly necessary.
The fact of the matter is that, compared to the costs that a breach of privacy will incur, the investment you put into your security measures will suddenly seem like a real bargain.
Chances are, you’ve gone through some old files, deleting what is no longer required. This is especially critical when you are upgrading your storage and getting rid of your existing storage media or an old computer. Let’s talk about what really happens when you’re doing so—chances are, you may be overlooking a serious security problem.