Small businesses are presented with the challenging prospect of monitoring and policing various IT-related policies that you might have for your network infrastructure and workplace technology use. The difficulty of this notion does little to lessen its importance. You need to take action to protect your assets, data, and reputation from the countless threats out there, and ensuring that your employees are properly using technology is paramount to this endeavor.
Macro Systems Blog
Mobile malware isn’t common, but it’s growing increasingly more so. You may have heard of a malware called XLoader, which has been utilized to victimize people in over seven countries. This mobile threat has seen various iterations over the past several years, but you should be especially concerned these days.
The effectiveness of your business' IT security heavily relies on the functionality of your IT operations. Making sure that your staff comprehends their role in safeguarding your business assets is critical. Let’s delve into the essential priorities for establishing a robust security training platform, an indispensable element in fortifying your business' IT defenses.
For the IT administrator and the small business owner, it can be a bewildering experience when your organization comes under siege from employee-induced cyberthreats; especially if you, like many other organizations, have started prioritizing security training. Even if the threat is thwarted early and the effect on the business is negligible, it is critical that you trust the people who have access to your organization’s digital resources. Listed below are some of the reasons some of your staff take cybersecurity initiatives worse than others.
It’s an unfortunate fact that all businesses will inherently face some type of threats during their operations; that’s inevitable. From cyberattacks to natural disasters to good, old-fashioned accidents, you’re liable to face no small risk. This risk makes a process known as risk mitigation so imperative for all businesses to undergo with some regularity.
Listed below are the aspects of creating and maintaining a dependable risk mitigation strategy.
You might have noticed that business insurance companies are starting to show an interest in how you are protecting your technology and data. If your org has been in touch with your insurance provider regarding modifying or renewing your business insurance, you were likely handed a lengthy questionnaire about your cybersecurity. Let’s take a look together to help you make informed decisions on how to handle your IT and how to prevent your insurance costs from skyrocketing.
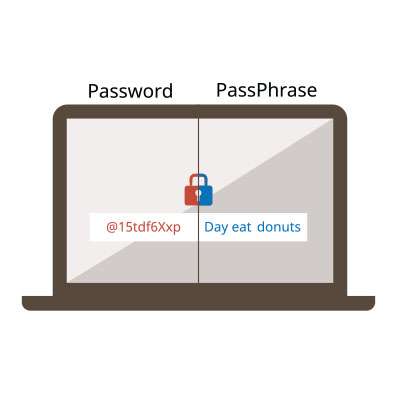
Passwords are the keys to digital access, but they're often not treated as keys; they aren’t always protected by their users. Alas, people don’t always do everything they can to protect their passwords and there are a lot more scammers out there than pickpockets.
Effective password management is imperative for any organization. It works to maintain the security of online accounts and sensitive information. Listed below are five ways to control and enhance your password management.
We’re hoping that you are reading this post to prepare yourself in case your organization were to face a ransomware attack, but if you are suffering from one right now, we encourage you to reach out to us immediately, whether you are a client or not. Ransomware spreads quickly, and once it has infected a system, there really isn’t much you can do to stop it. That being said, there are steps you need to take to come back from this gracefully.
Unfortunately, some of the biggest retail days of the year are some of the biggest days for scams, the entire holiday season seeing an increase in threats toward retailers and, as a result, the consumers that are just looking for that perfect gift for their loved ones. Listed below are some statistics and trends to see what insights we can glean.
With ransomware becoming one of the most damaging threats out there for small businesses, it’s more critical than ever to know how to protect your organization from its influence. Fortunately, there are measures you can take, including some very powerful ones like zero-trust policies that can thwart attempted ransomware attacks.
With data security being a hot commodity with hackers, it’s no surprise that companies want to do everything they can to protect their assets. One method for doing so is implementing a Virtual Private Network, or VPN, that can effectively obfuscate data while it’s in transit. Listed below are some of the most valuable reasons why your business should be using a VPN.
Constant challenges arise for businesses, ranging from supply chain disruptions and employee turnover to the unpredictable forces of natural disasters. Among these challenges, cyberattacks stand out as an inconspicuous yet highly menacing threat. Listed below are the various ways cyberattacks endanger your business and how to prepare for them effectively.
Social media scams encompass fraudulent activities and deceptive schemes that occur across numerous social media platforms. These scams target users on platforms like Facebook, X (formerly Twitter), LinkedIn, and various others, irrespective of their age or background. They exploit individuals' trust, curiosity, or lack of awareness. Social media scams manifest in various forms, and the following are some common examples.