There are many, many different versions of cybercrime that businesses need to be vigilant about. That being said, most of them can mostly be avoided through a few basic practices and behaviors. Listed below are a few tips to help you prevent attacks from successfully influencing your business, so make sure you share them with your entire team, as well.
Macro Systems Blog
One of the great obstacles many companies have regarding remote work is the fact that, well, the team will be remote—not in the office, safely under supervision. This has led many to consider using the webcams installed in their employees’ devices to keep tabs on them. This idea of monitoring your team is discussed below, as well as why it probably isn’t a good one.
In the recent past, connectivity required an actual, physical connection between two endpoints. As a result, a wired connection was the only option for businesses to access online materials and resources. This leaves businesses with a choice to make: is a wired connection better for my operations, or should I implement wireless connectivity?
The COVID-19 pandemic has shown us that not all businesses have considered how to be flexible in their operations, but it has also given them opportunities to adjust accordingly. With these new flexibilities in place, what does the future of your office look like? Would you ever consider a hybrid approach to the workplace?
March 18th is Global Recycling Day, which is intended to remind us of all the materials that can be reused in everyday life, in part as a way to decrease our individual carbon footprint. Having said that, it's valuable to know how much your business contributes in terms of its carbon footprint… and, once you know that figure, how you can minimize it.
We’ve all seen our friends and family sharing quizzes on their social media profiles, prompting people to find out what their celebrity stage name or what Hogwarts house you would be in. These fun, lighthearted quizzes are a solid way to get to know a little more about the people we’re connected with… and that’s the biggest issue.
Modern remote workers are constantly asked to endure meetings over their organization’s chosen video conferencing applications and while it may not be an ideal situation to improve the collaborative flow of your team, there are certain variables that you can control to get the most out of these virtual meetings.
Gauging the effectiveness of your cybersecurity can be a daunting task, especially when asking if it could make a significant difference in protecting your organization’s network infrastructure. If you want to track and measure your business’ cybersecurity preparedness, here are four steps to help you perform an evaluation.
With so many great smartphones on the market, there are going to be a couple that stand out for being innovative and interesting in their designs. These devices, many of which fall into the foldable category, are pretty cool and worth looking into. Here are some of the better options on the market now.
A lot of people like to make predictions about what the future will bring for business, many of which are based on anecdotes and hopes. When it comes to information system management and the future of IT for business, there are a lot of claims made by companies looking to take advantage of the reliance on IT and present business owners’ and decision makers’ options on how to leverage this technology for their own good. Listed below is a look at three emerging technologies that we will all come to use in the future and whether they are right for your business now.
Collaboration is not just nice, it is the only way many businesses can afford to keep the lights on. Comprehending that truth makes it critical to find the best strategies and technologies to support your staff’s collaborative endeavors. Listed below is a look at a few options to help enhance your business’ collaboration.
Businesses usually struggle with the hardware side of running a business, whether it is locating the right solutions or taking care of them. Hardware like server units, workstations, and networking components are what keep your company functioning, and without it, you don’t have much of a business. How can you make sure that your business is addressing this critical aspect of running a business? How can you keep hardware from breaking your budget? We recommend starting with a network audit.
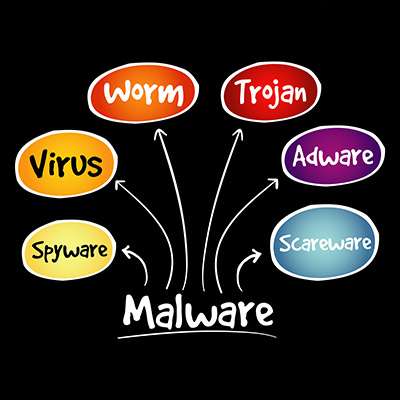
Network security could mean a number of things, but usually people are using the term as a blanket statement against the dreaded idea of malware and its numerous forms. Listed below is a discussion on how vast the world of malware can be and how often you might find yourself misunderstanding what it exactly is. Comprehending all this can help you identify if you have become a malware victim or not.
Keeping a secure password is a little confusing these days, especially when the standards for what is an acceptable, complex password seem to keep shifting back and forth. Let’s take a look at some of the industry-standard best practices for passwords and how you can implement them for your business.
Microsoft has planned a rise in the price of its software offerings Microsoft 365 and Office 365; it will impact your business in some way whether you are ready or not. We are writing this blog to share information that you might find imperative about this price increase so you can plan to get the most out of your software moving forward.
The Internet of Things is an amalgamation of countless connected devices that all perform numerous functions. Many of these devices are being utilized in ways that businesses never thought possible. In fact, the Internet of Things and its boundless amount of connected devices have given manufacturers and corporations even more opportunities to get birds-eye views of operations, inventory management, and supply chain management.